Services
Managed Security
Peregrine
Security Tools Monitoring Management
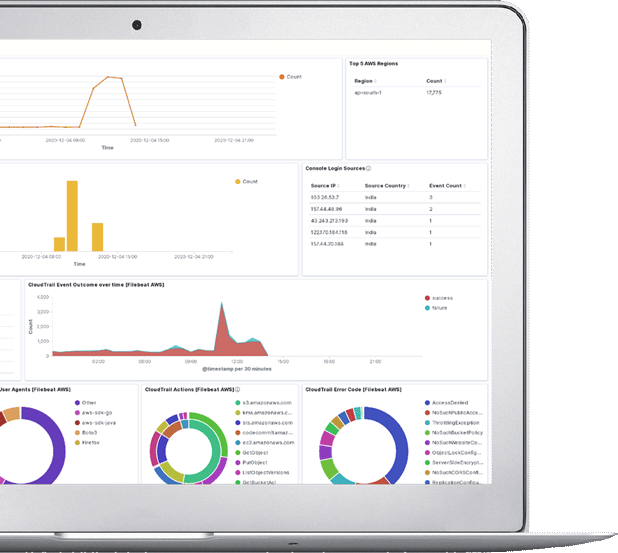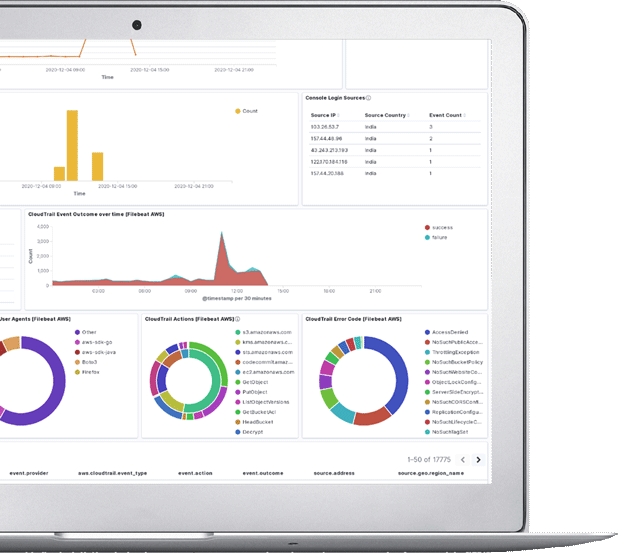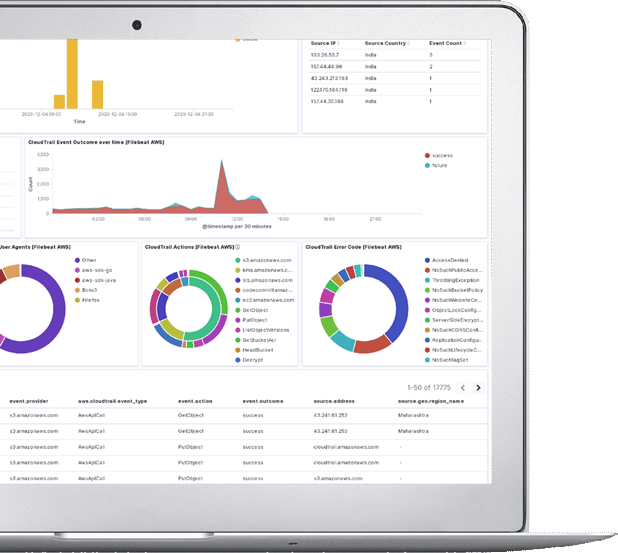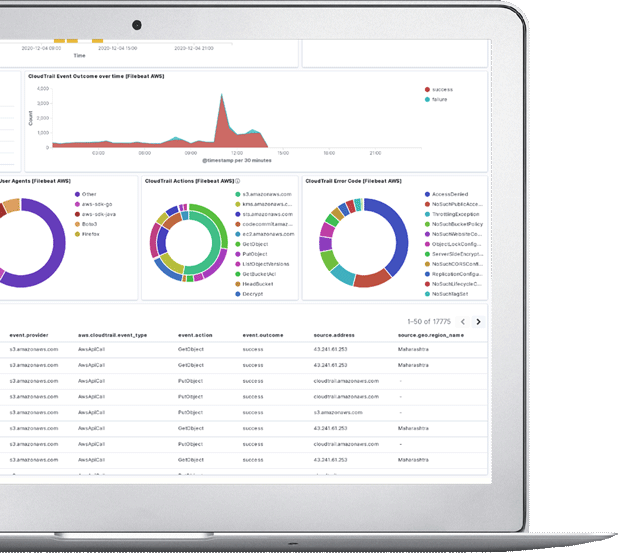
Organisation's invest in expensive security tools and technologies however it is important to ensure that they are configured and managed appropriately. Maintaining best practices and health of the tool is very important for getting the best value from the tools. CyberNX remote services help customers to manage or monitor the security infrastructure or tools continuously.
Peregrine
Remote Vulnerability, Web Security Monitoring
As organisations are continuously building and deploying web facing assets. It is important to maintain the security of the assets. How do we ensure that the assets are securely configured, patched and security of the assets are maintained as per best practices? CyberNX's remote vulnerability program for web facing assets helps the organisations to monitor the public assets continuously at a very low cost.
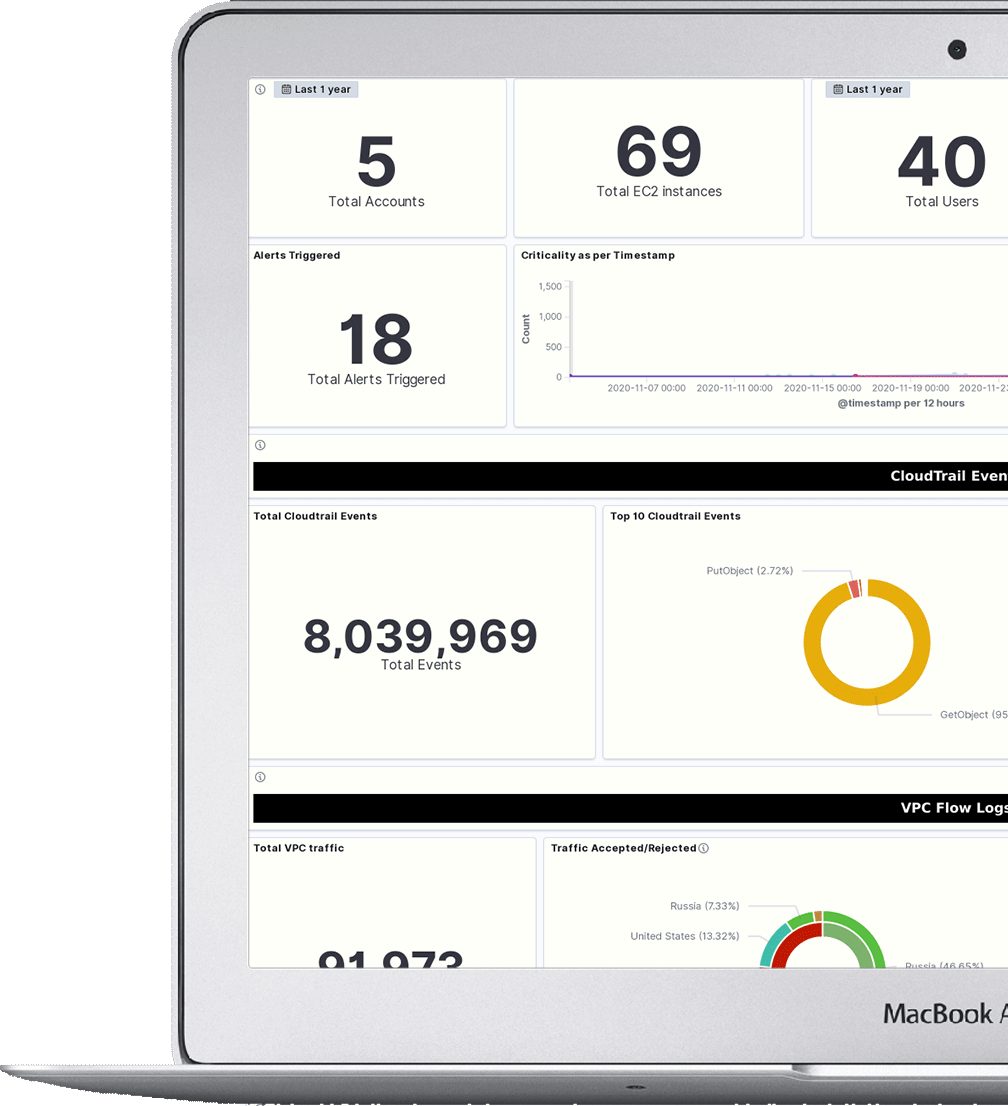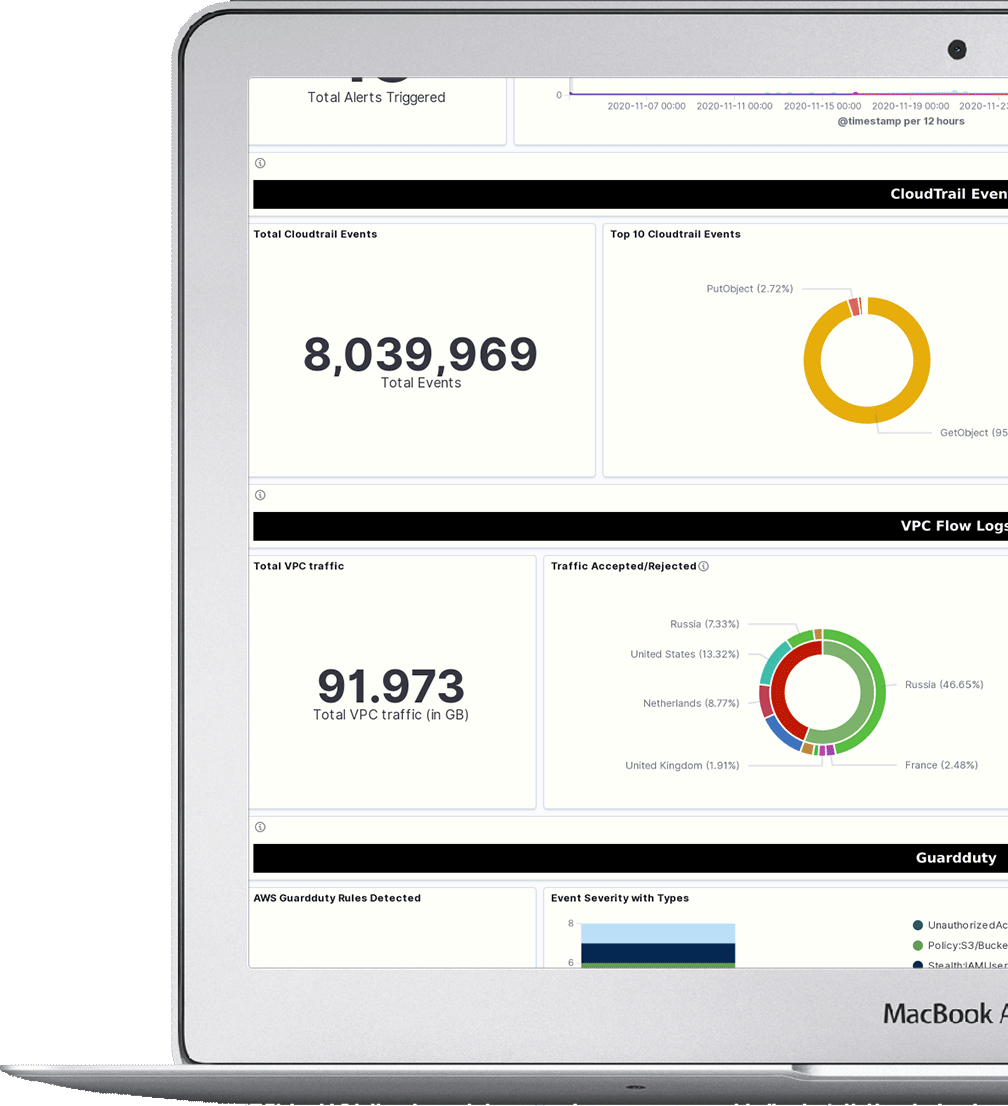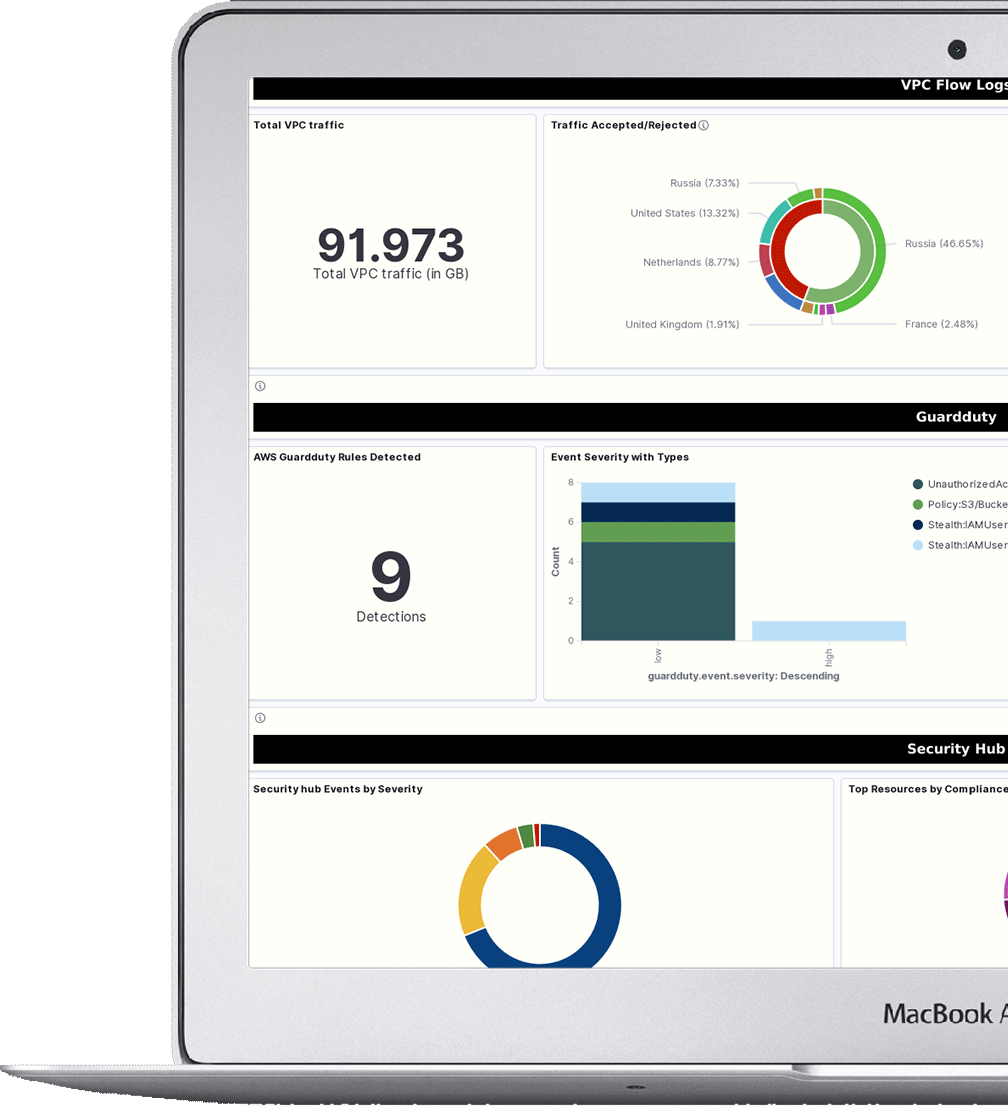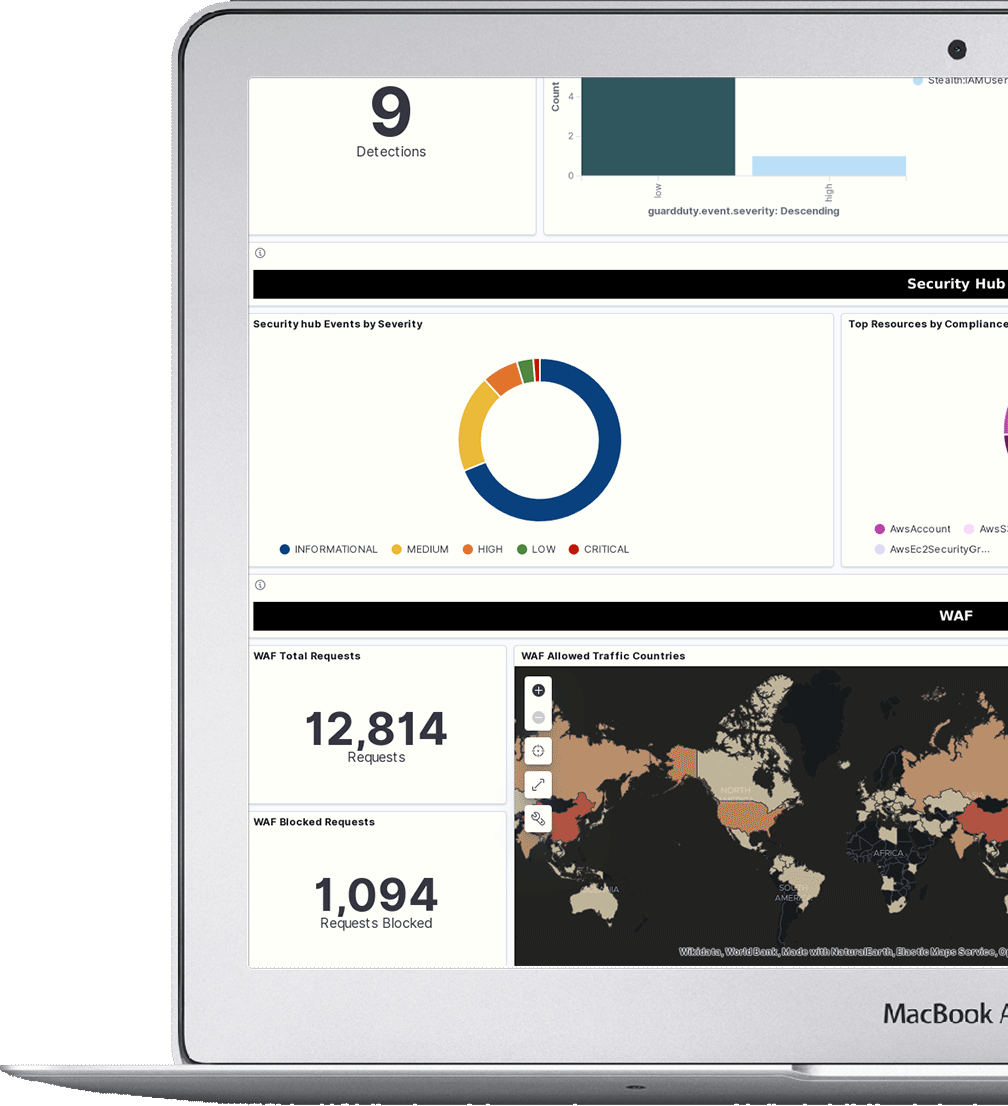
Peregrine
Brand Risk Monitoring
Today many organisations are facing issues related to fake websites, domain names registered. Many of the frauds committed today are related to fake sites or domains. Hence creating digital assets online also requires adequate protection and monitoring of possible abuse. The service helps to continuously monitor the brand risks an organisation is facing.
Peregrine
Managed Security Services in a Nut Shell
Prevent
Exposures
Continuously scan your infrastructure applications from the internet from vulnerabilities. Option to run scans daily or weekly.
Digital
Risks
Monitor your brand, fake sites, applications, leaked credentials etc. Detect brand abuse before it becomes a major issue.
Secure Infrastructure
Security tools must be implemented and configured appropriately. Applying best practices on infrastructure and applications.
Monitor
Cloud
Continuously scan your cloud infrastructure for finding vulnerabilities or misconfigurations. Monitor Cloud misconfigurations to prevent misuse.
Improve Awareness
Employees are often targeted to get inside an organization. They are considered as the weakest link. We must continuously train and communicate about the latest threats.
FAQ's
Some Questions
And Their Answers
Will Peregrine Implement a 24 X 7 Cyber Security Operations?
We will implement a comprehensive Cyber Security Monitoring to continuously monitor your key assets.
How Peregrine can help customers to enhance theis Security Maturity?
We believe in creating a healthy Cyber Security Posture. Based on your observations we will work with you to improve overall Security Posture.
What is Comprehensive Cyber Security Services Range Peregrine can provides?
We can provide all Cyber Security requirements and assign dedicated program managers to work with you continuously.
Will Peregrine Continously Engagement with their Clients?
We are looking to engage with our clients continuously and partner them in their journey. We assign dedicated customer success managers to ensure effectiveness.
